

Sign Up
What is best time for the call?
Oops! Something went wrong while submitting the form.
%20Solutions%20for%20Secure%20Access.png)
Traditional perimeter-based security models no longer suffice in today’s hybrid work, multi-cloud infrastructure, and rampant cyber threats. The era of “castle-and-moat” defenses, where everything inside the network is trusted, is over.
As enterprise applications move outside the data center and users connect from everywhere, organizations need a modern access model that hides internal resources from unauthorized access and dynamically adapts to risk context. That’s where Software-Defined Perimeter (SDP) comes in.
SDP solutions implement a zero-trust approach by verifying user identity and device posture before granting access to applications, not networks. They render applications invisible to unauthorized users, significantly reducing the attack surface.
In this 2025 guide, we break down the top 10 software-defined perimeter solutions, compare their features, deployment models, and use cases, and explore how to implement SDP effectively for secure access across on-prem, cloud, and hybrid environments.
A Software-Defined Perimeter is a security model that enforces application-level access based on identity and device context rather than granting broad network access like a VPN.
Key Principles of SDP:
SDP vs. VPN vs. Traditional Security
SDP is the foundational architecture for Zero Trust Network Access (ZTNA), aligned with NIST SP 800-207.
When evaluating SDP solutions in 2025, look for the following capabilities:
Overview:
ZPA is a cloud-delivered, zero-trust access solution that connects users directly to applications without ever placing them on the network. It leverages identity and context to ensure that only authorized users and devices can access specific apps.
Key Features:
Strengths:
Weaknesses:
Ideal Use Case / Industry Fit:
Perfect for large enterprises with distributed workforces and sensitive workloads in regulated environments.
G2 Rating: 4.5 / 5 (65 reviews)
Gartner Peer Insights Rating: 4.7 / 5 (136 reviews)
Screenshot:

Overview:
EAA offers secure remote access to internal apps without a VPN. It acts as a reverse proxy and implements pre-authentication, cloaking apps until users are verified.
Key Features:
Strengths:
Weaknesses:
Ideal Use Case / Industry Fit:
It is best for enterprises seeking a unified access model for web and internal apps, especially those using Akamai for web performance.
G2 Rating: 4.4 / 5 (22 reviews)
Gartner Peer Insights Rating: 4.4 / 5 (13 reviews)
Screenshot:

Overview:
Perimeter 81 delivers a unified network security platform with SDP, ZTNA, FWaaS, and SWG in one interface. Its simplicity makes it a favorite among small to mid-sized businesses.
Key Features:
Strengths:
Weaknesses:
Ideal Use Case / Industry Fit:
It is ideal for SMBs and scaling SaaS firms that want ZTNA without a complex setup.
G2 Rating: 4.7 / 5 (117 reviews)
Gartner Peer Insights Rating: 4.7 / 5 (170 reviews)
Screenshot:

Overview:
Tailscale offers a peer-to-peer mesh VPN built on WireGuard, a minimalist, developer-friendly SDP platform.
Key Features:
Strengths:
Weaknesses:
Ideal Use Case / Industry Fit:
Ideal for tech-forward SMBs, DevOps teams, and remote-first engineering orgs.
G2 Rating: 4.7 / 5 (17 reviews)
Screenshot:

Overview:
Appgate’s enterprise-grade SDP platform enforces identity-centric, risk-aware access with deep compliance support, making it popular in regulated industries.
Key Features:
Strengths:
Weaknesses:
Ideal Use Case / Industry Fit:
It is ideal for financial services, government agencies, and health orgs managing regulated workloads.
G2 Rating: 4.8 / 5 (28 reviews)
Gartner Peer Insights Rating: 4.7 / 5 (40 reviews)
Screenshot:

Overview:
Part of Cloudflare’s integrated Zero Trust platform, it provides secure, fast access to apps without VPNs or exposed IPs.
Key Features:
Strengths:
Weaknesses:
Ideal Use Case / Industry Fit:
Excellent for cloud-first companies prioritizing speed, simplicity, and global scale.
G2 Rating: 4.6 / 5 (92 reviews)
Gartner Peer Insights Rating: 4.5 / 5 (205 reviews)
Screenshot:

Overview:
Cato’s platform merges SDP with SASE and SD-WAN, creating a fully converged cloud-native secure access experience.
Key Features:
Strengths:
Weaknesses:
Ideal Use Case / Industry Fit:
Great for large global orgs with branch offices and WAN complexities.
G2 Rating: 4.4 / 5 (73 reviews)
Gartner Peer Insights Rating: 4.6 / 5 (107 reviews)
Screenshot:

Overview:
NetMotion provides an SDP platform with real-time visibility into network conditions and device behaviors.
Key Features:
Strengths:
Weaknesses:
Ideal Use Case / Industry Fit:
Well-suited for law enforcement, public agencies, and mobile-first industries.
G2 Rating: 4.7 / 5 (213 reviews)
Gartner Peer Insights Rating: 4.5 / 5 (151 reviews)
Screenshot:

Overview:
Teleport is designed for secure infrastructure access, SSH, Kubernetes, databases, with audit, identity, and policy baked in.
Key Features:
Strengths:
Weaknesses:
Ideal Use Case / Industry Fit:
Best for platform engineering teams, cloud-native ops, and internal infra access.
G2 Rating: 4.5 / 5 (104 reviews)
Gartner Peer Insights Rating: 4.7 / 5 (30 reviews)
Screenshot:
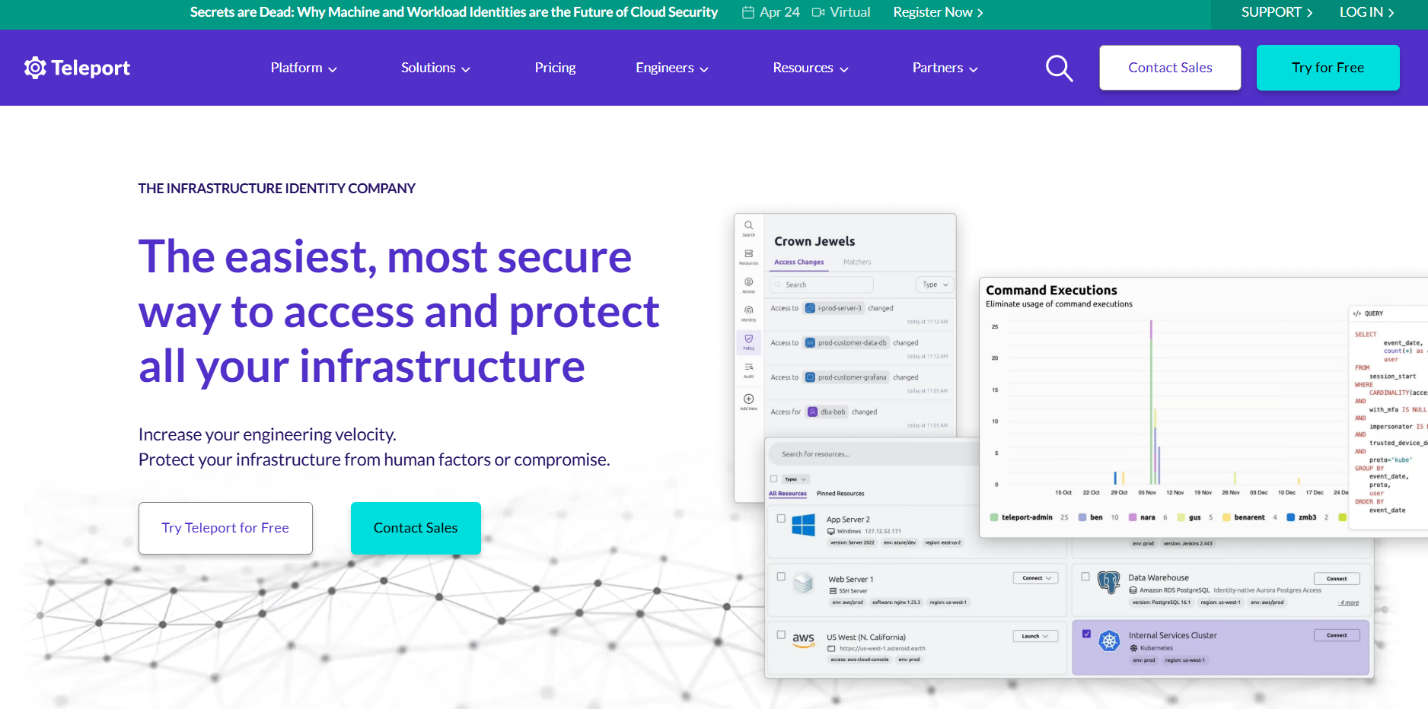
Overview:
iboss delivers zero trust access from a globally distributed cloud edge. It supports deep inspection and integrates with DLP, SWG, and malware prevention engines.
Key Features:
Strengths:
Weaknesses:
Ideal Use Case / Industry Fit:
It is best for multinational enterprises needing robust, layered security at scale.
G2 Rating: 4.0 / 5 (15 reviews)
Gartner Peer Insights Rating: 4.8 / 5 (129 reviews)
Screenshot:

Q1. Is SDP the same as ZTNA?
SDP is the foundation for ZTNA, enabling per-app access control that is aligned with zero trust.
Q2. Does SDP replace VPN?
Yes, SDP eliminates the need for VPNs by providing more secure, granular access.
Q3. Can SDP support on-prem applications?
Absolutely. Many SDP tools offer connectors or agents for on-prem access.
Q4. What compliance frameworks do SDP tools help with?
SOC 2, ISO 27001, HIPAA, PCI-DSS, NIST 800-207, GDPR.
Deploying SDP is just the first step; maintaining visibility is critical. Without continuous governance, access sprawl can reintroduce risks.
That’s where CloudNuro.ai plays a key role:
Software-Defined Perimeter solutions are essential for building zero-trust access in a remote-first, cloud-native world. The tools listed above provide flexible, scalable ways to protect your applications, no matter where they live.
✅ Want deeper insights into how your SDP, IAM, and SaaS policies intersect?
✅ Need help uncovering hidden risks and license waste across access layers?
CloudNuro.ai empowers your security team with real-time visibility, actionable governance metrics, and optimization insights.
📌 Book Your Free Demo Now and optimize secure access governance across your cloud environment.
Request a no cost, no obligation free assessment —just 15 minutes to savings!
Get StartedTraditional perimeter-based security models no longer suffice in today’s hybrid work, multi-cloud infrastructure, and rampant cyber threats. The era of “castle-and-moat” defenses, where everything inside the network is trusted, is over.
As enterprise applications move outside the data center and users connect from everywhere, organizations need a modern access model that hides internal resources from unauthorized access and dynamically adapts to risk context. That’s where Software-Defined Perimeter (SDP) comes in.
SDP solutions implement a zero-trust approach by verifying user identity and device posture before granting access to applications, not networks. They render applications invisible to unauthorized users, significantly reducing the attack surface.
In this 2025 guide, we break down the top 10 software-defined perimeter solutions, compare their features, deployment models, and use cases, and explore how to implement SDP effectively for secure access across on-prem, cloud, and hybrid environments.
A Software-Defined Perimeter is a security model that enforces application-level access based on identity and device context rather than granting broad network access like a VPN.
Key Principles of SDP:
SDP vs. VPN vs. Traditional Security
SDP is the foundational architecture for Zero Trust Network Access (ZTNA), aligned with NIST SP 800-207.
When evaluating SDP solutions in 2025, look for the following capabilities:
Overview:
ZPA is a cloud-delivered, zero-trust access solution that connects users directly to applications without ever placing them on the network. It leverages identity and context to ensure that only authorized users and devices can access specific apps.
Key Features:
Strengths:
Weaknesses:
Ideal Use Case / Industry Fit:
Perfect for large enterprises with distributed workforces and sensitive workloads in regulated environments.
G2 Rating: 4.5 / 5 (65 reviews)
Gartner Peer Insights Rating: 4.7 / 5 (136 reviews)
Screenshot:

Overview:
EAA offers secure remote access to internal apps without a VPN. It acts as a reverse proxy and implements pre-authentication, cloaking apps until users are verified.
Key Features:
Strengths:
Weaknesses:
Ideal Use Case / Industry Fit:
It is best for enterprises seeking a unified access model for web and internal apps, especially those using Akamai for web performance.
G2 Rating: 4.4 / 5 (22 reviews)
Gartner Peer Insights Rating: 4.4 / 5 (13 reviews)
Screenshot:

Overview:
Perimeter 81 delivers a unified network security platform with SDP, ZTNA, FWaaS, and SWG in one interface. Its simplicity makes it a favorite among small to mid-sized businesses.
Key Features:
Strengths:
Weaknesses:
Ideal Use Case / Industry Fit:
It is ideal for SMBs and scaling SaaS firms that want ZTNA without a complex setup.
G2 Rating: 4.7 / 5 (117 reviews)
Gartner Peer Insights Rating: 4.7 / 5 (170 reviews)
Screenshot:

Overview:
Tailscale offers a peer-to-peer mesh VPN built on WireGuard, a minimalist, developer-friendly SDP platform.
Key Features:
Strengths:
Weaknesses:
Ideal Use Case / Industry Fit:
Ideal for tech-forward SMBs, DevOps teams, and remote-first engineering orgs.
G2 Rating: 4.7 / 5 (17 reviews)
Screenshot:

Overview:
Appgate’s enterprise-grade SDP platform enforces identity-centric, risk-aware access with deep compliance support, making it popular in regulated industries.
Key Features:
Strengths:
Weaknesses:
Ideal Use Case / Industry Fit:
It is ideal for financial services, government agencies, and health orgs managing regulated workloads.
G2 Rating: 4.8 / 5 (28 reviews)
Gartner Peer Insights Rating: 4.7 / 5 (40 reviews)
Screenshot:

Overview:
Part of Cloudflare’s integrated Zero Trust platform, it provides secure, fast access to apps without VPNs or exposed IPs.
Key Features:
Strengths:
Weaknesses:
Ideal Use Case / Industry Fit:
Excellent for cloud-first companies prioritizing speed, simplicity, and global scale.
G2 Rating: 4.6 / 5 (92 reviews)
Gartner Peer Insights Rating: 4.5 / 5 (205 reviews)
Screenshot:

Overview:
Cato’s platform merges SDP with SASE and SD-WAN, creating a fully converged cloud-native secure access experience.
Key Features:
Strengths:
Weaknesses:
Ideal Use Case / Industry Fit:
Great for large global orgs with branch offices and WAN complexities.
G2 Rating: 4.4 / 5 (73 reviews)
Gartner Peer Insights Rating: 4.6 / 5 (107 reviews)
Screenshot:

Overview:
NetMotion provides an SDP platform with real-time visibility into network conditions and device behaviors.
Key Features:
Strengths:
Weaknesses:
Ideal Use Case / Industry Fit:
Well-suited for law enforcement, public agencies, and mobile-first industries.
G2 Rating: 4.7 / 5 (213 reviews)
Gartner Peer Insights Rating: 4.5 / 5 (151 reviews)
Screenshot:

Overview:
Teleport is designed for secure infrastructure access, SSH, Kubernetes, databases, with audit, identity, and policy baked in.
Key Features:
Strengths:
Weaknesses:
Ideal Use Case / Industry Fit:
Best for platform engineering teams, cloud-native ops, and internal infra access.
G2 Rating: 4.5 / 5 (104 reviews)
Gartner Peer Insights Rating: 4.7 / 5 (30 reviews)
Screenshot:

Overview:
iboss delivers zero trust access from a globally distributed cloud edge. It supports deep inspection and integrates with DLP, SWG, and malware prevention engines.
Key Features:
Strengths:
Weaknesses:
Ideal Use Case / Industry Fit:
It is best for multinational enterprises needing robust, layered security at scale.
G2 Rating: 4.0 / 5 (15 reviews)
Gartner Peer Insights Rating: 4.8 / 5 (129 reviews)
Screenshot:

Q1. Is SDP the same as ZTNA?
SDP is the foundation for ZTNA, enabling per-app access control that is aligned with zero trust.
Q2. Does SDP replace VPN?
Yes, SDP eliminates the need for VPNs by providing more secure, granular access.
Q3. Can SDP support on-prem applications?
Absolutely. Many SDP tools offer connectors or agents for on-prem access.
Q4. What compliance frameworks do SDP tools help with?
SOC 2, ISO 27001, HIPAA, PCI-DSS, NIST 800-207, GDPR.
Deploying SDP is just the first step; maintaining visibility is critical. Without continuous governance, access sprawl can reintroduce risks.
That’s where CloudNuro.ai plays a key role:
Software-Defined Perimeter solutions are essential for building zero-trust access in a remote-first, cloud-native world. The tools listed above provide flexible, scalable ways to protect your applications, no matter where they live.
✅ Want deeper insights into how your SDP, IAM, and SaaS policies intersect?
✅ Need help uncovering hidden risks and license waste across access layers?
CloudNuro.ai empowers your security team with real-time visibility, actionable governance metrics, and optimization insights.
📌 Book Your Free Demo Now and optimize secure access governance across your cloud environment.
Request a no cost, no obligation free assessment - just 15 minutes to savings!
Get StartedWe're offering complimentary ServiceNow license assessments to only 25 enterprises this quarter who want to unlock immediate savings without disrupting operations.
Get Free AssessmentGet Started

Recognized Leader in SaaS Management Platforms by Info-Tech SoftwareReviews
